In today’s growing world of DevOps, big player are started implementing business processes on IaC (Infrastructure as Code). IaC work as to simplify the process of large-scale management. Modern IaC tools simplify the configuration to resolve server problems in a quick time.
Terraform and Ansible are two popular frontline line DevOps tools that provision and configure servers. Ansible is the more mature between the two, originating in early 2012 and Terraform is a Hashicorp product and was first introduce in 2014. As the DevOps industry is gaining momentum, so also Ansible and Terraform gaining their popularity with this trend. Both the tools used in deploying the code and infrastructure, in simple Ansible acts as a configuration management solution, Terraform is a service orchestration tool.
In this blog, we point our focus on Terraform vs Ansible, a discussion that is highly dominating the current DevOps market. Let’s first known about these tools:
What is Ansible?

Ansible is an open-source automation tool, or you can also called platform, used for IT tasks such as configuration management, application deployment, intraservice orchestration, and provisioning. Automation is crucial these days, with IT environments that are too complex and often need to scale too quickly for system administrators and developers to keep up if they had to do everything manually.
In simple words, it frees up time and increases efficiency. And also it is rapidly rising to the top in the world of automation tools.
Benefits of Ansible
- Free: Ansible is an open-source tool.
- Very simple to set up and use: No special coding skills are necessary to use Ansible’s playbooks.
- Powerful: Ansible lets you model even highly complex IT workflows.
- Flexible: Orchestrate the entire application environment no matter where it’s deployed. You can also customize it based on your needs.
- Agentless: No need to install any other software or firewall ports on the client systems you want to automate. You also don’t have to set up a separate management structure.
- Efficient: You don’t need to install any extra software, there’s more room for application resources on your server.
What is Terraform?

Terraform is an open source, CLI-based infrastructure as code tool created by Hashicorp.
Terraform is an infrastructure as code tool that helps you to build, change, and infrastructure safely and efficiently. This process includes low-level components such as compute instances, storage, and networking, as well as high-level components such as DNS entries, SaaS features, etc. Terraform can manage both existing service providers and custom in-house solutions.
Benefits of Using Terraform
So now you know what Terraform is and how it works, let’s take a look on the top reasons why you should start using Terraform today:
- Improve multi-cloud infrastructure deployment
- Automated infrastructure management
- Infrastructure as code
- Reduced development costs
- Reduced time to provision
What is the difference between terraform and Ansible?
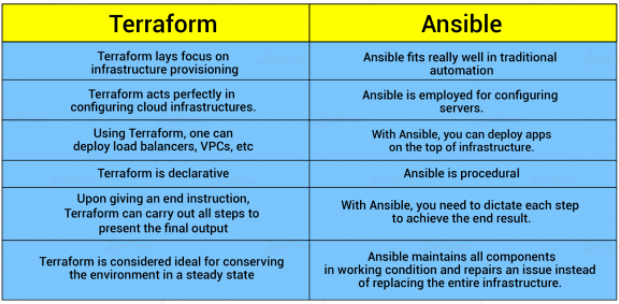
In this section, let’s check the difference between the two. Meanwhile both are designed for similar purposes, both have definitely laid a foundation for lifecycle management frameworks. Now, both our players in their battle has placed their cards on the table. Let us find out their differences on some of major factors:
Conclusion
The possibility of a perfect answer on “Why Terraform” or “Why not Ansible” depends mainly on your requirements. Both the tools have so many similarities and also some fair differences as well. So, which one is the best? From a practical perspective, it is advisable to use Ansible for configuration management and Terraform for orchestration. The primary purpose of Terraform is orchestration, and it is considerably intuitive.
Also from career aspect, opportunities for these skilled professionals are increasing significantly with huge scope for career growth.
According to Indeed.com, the average salary of a professional of these skills is $177,530 per annum.
Both Ansible and Terraform are the leading data analytics tool which is adopted by many MNCs worldwide. With this, the demand for the professionals is gradually.
Below you can watch and learn Ansible and Terraform Tutorials
Ansible Advance Tutorial – Intro, Adhoc Command, Inventory, Playbook
Terraform Basic Tutorial with Demo
Hope you find this answer helpful.