When your container is not getting a internet issues, it must be issues with DNS nameserver. please try following…
Error
0% [Connecting to archive.ubuntu.com] [Connecting to security.ubuntu.com
Ign:2 http://security.ubuntu.com/ubuntu jammy-security InRelease
Ign:4 http://archive.ubuntu.com/ubuntu jammy-backports InRelease
Ign:2 http://security.ubuntu.com/ubuntu jammy-security InRelease
Ign:1 http://archive.ubuntu.com/ubuntu jammy InRelease
Err:2 http://security.ubuntu.com/ubuntu jammy-security InRelease
Temporary failure resolving 'security.ubuntu.com'
Ign:3 http://archive.ubuntu.com/ubuntu jammy-updates InRelease
Ign:4 http://archive.ubuntu.com/ubuntu jammy-backports InRelease
Ign:1 http://archive.ubuntu.com/ubuntu jammy InRelease
Ign:3 http://archive.ubuntu.com/ubuntu jammy-updates InRelease
Ign:4 http://archive.ubuntu.com/ubuntu jammy-backports InRelease
Err:1 http://archive.ubuntu.com/ubuntu jammy InRelease
Temporary failure resolving 'archive.ubuntu.com'
Err:3 http://archive.ubuntu.com/ubuntu jammy-updates InRelease
Temporary failure resolving 'archive.ubuntu.com'
W: Failed to fetch http://archive.ubuntu.com/ubuntu/dists/jammy/InRelease Temporary failure resolving 'archive.ubuntu.com'
W: Failed to fetch http://archive.ubuntu.com/ubuntu/dists/jammy-updates/InRelease Temporary failure resolving 'archive.ubuntu.com'
W: Failed to fetch http://archive.ubuntu.com/ubuntu/dists/jammy-backports/InRelease Temporary failure resolving 'archive.ubuntu.com'
W: Failed to fetch http://security.ubuntu.com/ubuntu/dists/jammy-security/InRelease Temporary failure resolving 'security.ubuntu.com'
W: Some index files failed to download. They have been ignored, or old ones used instead.Solution
In DOCKER HOST VM
First thing to check is run cat /etc/resolv.conf in the docker container. If it has an invalid DNS server, such as nameserver 127.0.x.x, then the container will not be able to resolve the domain names into ip addresses, so ping google.com will fail.
Second thing to check is run cat /etc/resolv.conf on the host machine. Docker basically copies the host’s /etc/resolv.conf to the container everytime a container is started. So if the host’s /etc/resolv.conf is wrong, then so will the docker container.
If you have found that the host’s /etc/resolv.conf is wrong, then you have 2 options:
- Hardcode the DNS server in daemon.json. This is easy, but not ideal if you expect the DNS server to change.
- Fix the hosts’s
/etc/resolv.conf. This is a little trickier, but it is generated dynamically, and you are not hardcoding the DNS server.
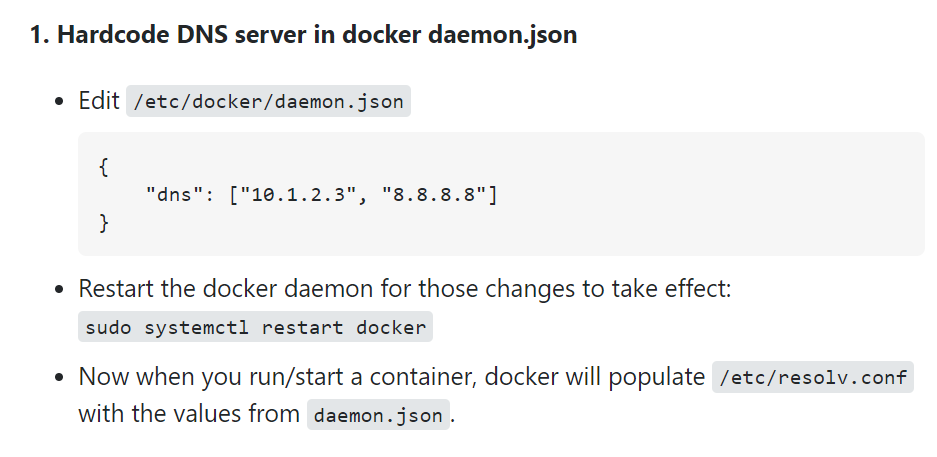
1. Hardcode DNS server in docker daemon.json
- Edit
/etc/docker/daemon.json{ "dns": ["10.1.2.3", "8.8.8.8"] } - Restart the docker daemon for those changes to take effect:
sudo systemctl restart docker - Now when you run/start a container, docker will populate
/etc/resolv.confwith the values fromdaemon.json.
2. Fix the hosts’s /etc/resolv.conf
A. Ubuntu 16.04 and earlier
- For Ubuntu 16.04 and earlier,
/etc/resolv.confwas dynamically generated by NetworkManager. - Comment out the line
dns=dnsmasq(with a#) in/etc/NetworkManager/NetworkManager.conf - Restart the NetworkManager to regenerate
/etc/resolv.conf:sudo systemctl restart network-manager - Verify on the host:
cat /etc/resolv.conf
B. Ubuntu 18.04 and later
- Ubuntu 18.04 changed to use
systemd-resolvedto generate/etc/resolv.conf. Now by default it uses a local DNS cache 127.0.0.53. That will not work inside a container, so Docker will default to Google’s 8.8.8.8 DNS server, which may break for people behind a firewall. /etc/resolv.confis actually a symlink (ls -l /etc/resolv.conf) which points to/run/systemd/resolve/stub-resolv.conf(127.0.0.53) by default in Ubuntu 18.04.- Just change the symlink to point to
/run/systemd/resolve/resolv.conf, which lists the real DNS servers:sudo ln -sf /run/systemd/resolve/resolv.conf /etc/resolv.conf - Verify on the host:
cat /etc/resolv.conf
Now you should have a valid /etc/resolv.conf on the host for docker to copy into the containers.