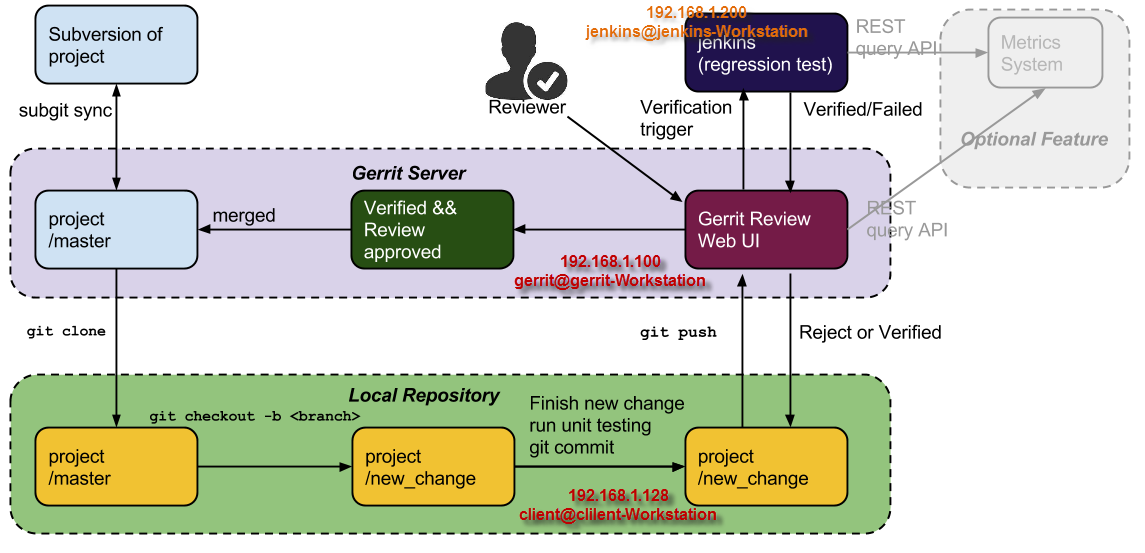
When Gerrit is configured as the central source repository, all code changes are sent to Pending Changes for others to review and discuss. When enough reviewers have approved a code change, you can submit the change to the code base.
In addition to the store of Pending Changes, Gerrit captures notes and comments made about each change. This enables you to review changes at your convenience or when a conversation about a change can’t happen in person. In addition, notes and comments provide a history of each change (what was changed and why and who reviewed the change).
Gerrit project is a workspace consisting of the following elements:
- Git repository: It is used to store the merged code base and the changes under review that have not being merged yet. Gerrit has the limitation of a single repository per project. There can also be projects without any code repository associated at all (that is, Security-only projects)
- Changes references under review: Git commit-id (expressed as SHA-1 Hexadecimal alphanumeric string) stored in the Gerrit DB and pointing to the corresponding changes stored in the Git repository. A Gerrit change is a Git commit object uploaded for review and associated to its comments and scores. It is stored in the project’s Git repository but it is not visible/accessible from the normal Git graph of commits, even it does start from a point on the commits graph.
- Access Control Lists (ACLs): It contains the list of roles defined for the Gerrit project and the associated access permissions to the Git repository branches.
- Prolog rules: It is the set of rules that govern the Code Review process for the project. 0 Additional metadata: All the extra settings such as description, merge strategy, contributor agreements, and accessory metadata needed in order to manage the project.
We have to make and review a change through these stages in Gerrit:
- Making the change.
- Creating the review.
- Reviewing the change.
- Reworking the change.
- Verifying the change.
- Submitting the change.