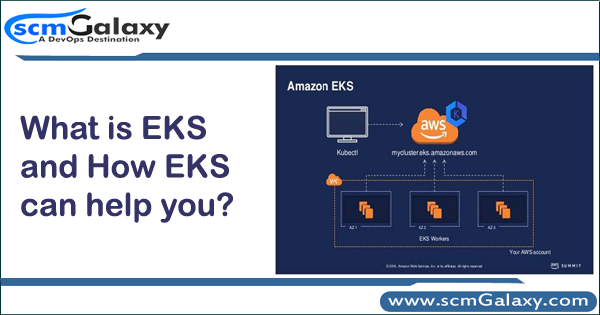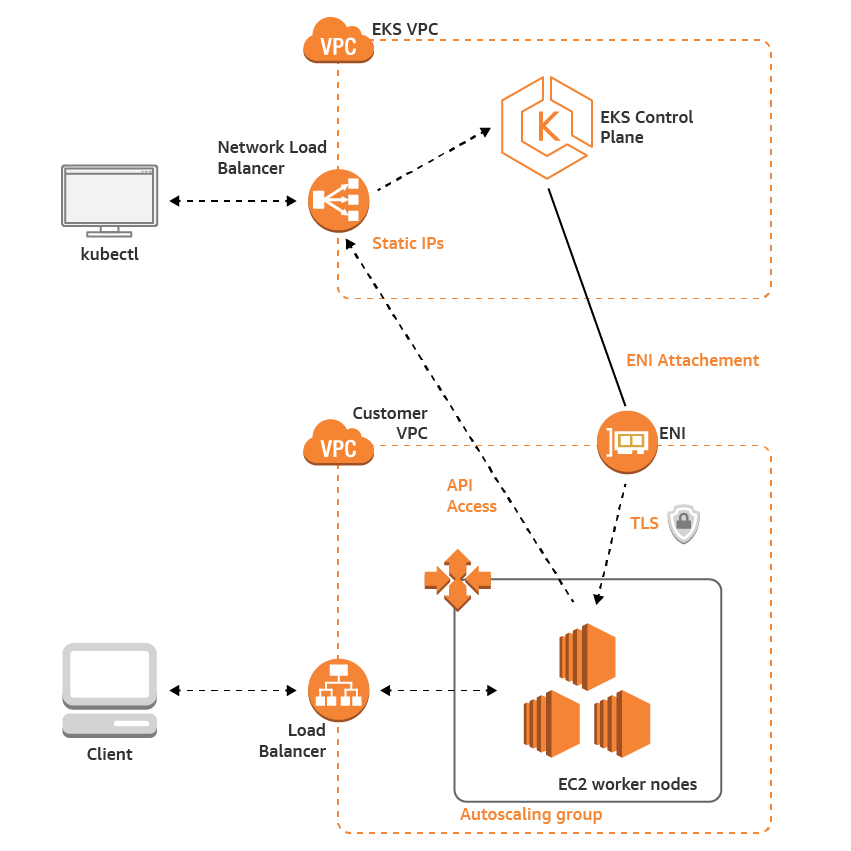
How to setup Kubernetes Dashboard in EKS using NodePort?
Step 1: Deploy the Dashboard
# Deploy the Kubernetes dashboard to your cluster:
kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/master/src/deploy/recommended/kubernetes-dashboard.yaml
# Deploy heapster to enable container cluster monitoring and performance analysis on your cluster:
$ kubectl apply -f https://raw.githubusercontent.com/kubernetes/heapster/master/deploy/kube-config/influxdb/heapster.yaml
# Deploy the influxdb backend for heapster to your cluster:
$ kubectl apply -f https://raw.githubusercontent.com/kubernetes/heapster/master/deploy/kube-config/influxdb/influxdb.yaml
# Create the heapster cluster role binding for the dashboard:
$ kubectl apply -f https://raw.githubusercontent.com/kubernetes/heapster/master/deploy/kube-config/rbac/heapster-rbac.yaml
Step 2: Create an eks-admin Service Account and Cluster Role Binding
# Create a file called eks-admin-service-account.yaml with the text below:
vi eks-admin-service-account.yaml apiVersion: v1 kind: ServiceAccount metadata: name: eks-admin namespace: kube-system $ kubectl apply -f eks-admin-service-account.yaml vi eks-admin-cluster-role-binding.yaml apiVersion: rbac.authorization.k8s.io/v1beta1 kind: ClusterRoleBinding metadata: name: eks-admin roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: cluster-admin subjects: - kind: ServiceAccount name: eks-admin namespace: kube-system $ kubectl apply -f eks-admin-cluster-role-binding.yaml
Step 3: Retrieve an authentication token
Retrieve an authentication token for the eks-admin service account. Copy the <authentication_token> value from the output. You use this token to connect to the dashboard.
kubectl -n kube-system describe secret $(kubectl -n kube-system get secret | grep eks-admin | awk '{print $1}')
Step 4: Connect to the Dashboard Via Node Port
Retrieve an authentication token for the eks-admin service account. Copy the <authentication_token> value from the output. You use this token to connect to the dashboard.
$ kubectl -n kube-system describe secret $(kubectl -n kube-system get secret | grep eks-admin | awk '{print $1}')
$ kubectl get pods --all-namespaces
$ kubectl get pods --namespace=kube-system
$ kubectl get svc --all-namespaces
$ kubectl edit svc/kubernetes-dashboard --namespace=kube-system
or
$ kubectl -n kube-system edit service kubernetes-dashboard
Just change "type: NodePort" only
# Please edit the object below. Lines beginning with a '#' will be ignored,
# and an empty file will abort the edit. If an error occurs while saving this file will be
# reopened with the relevant failures.
#
apiVersion: v1
kind: Service
metadata:
creationTimestamp: 2018-07-27T10:22:50Z
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
resourceVersion: "3288196"
selfLink: /api/v1/namespaces/kube-system/services/kubernetes-dashboard
uid: 03f2f747-9187-11e8-9432-02b761c0deac
spec:
clusterIP: 10.100.194.75
externalTrafficPolicy: Cluster
ports:
- nodePort: 30530
port: 443
protocol: TCP
targetPort: 8443
selector:
k8s-app: kubernetes-dashboard
sessionAffinity: None
type: NodePort
status:
loadBalancer: {}
$ kubectl describe pods kubernetes-dashboard-7d5dcdb6d9-mt9b9 --namespace=kube-system
#Find which node is running and get a Port of SVC
$ kubectl get svc --all-namespaces
$ kubectl get pods --all-namespaces
$ kubectl describe pods kubernetes-dashboard-7d5dcdb6d9-h9dcb --namespace=kube-system
Step 5: Connect to the Dashboard Via ClustorIP and Proxy
http://localhost:8001/api/v1/namespaces/kube-system/services/https:kubernetes-dashboard:/proxy/
https://10.16.39.28:30178/
IMPORTANT – Kubernetes Dashboard should be HTTPS