Is there a future in Ansible?
It is clear that, we live in the age of microservices, where automation is not a nice-to-have anymore. Cloud provisioning is an important element of the modern cloud computing model and it became an important to do list in every operation. There are so many different type of automation tools for job done. Those tools will help us in saving time and increasing the performance and accuracy of provisioning and configuration management processes that lead us to no human error process.
In this blog, we will discuss about one the most popular automation tool “Ansible” and also benefits of cloud automation with Ansible. Let’s first look at what is Ansible?
What is Ansible?
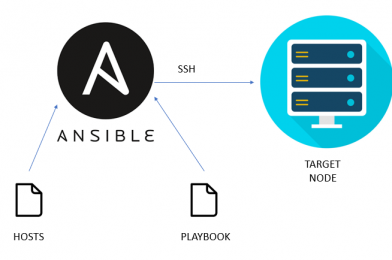
Ansible is an open-source automation tool, or you can also called platform, used for IT tasks such as configuration management, application deployment, intraservice orchestration, and provisioning. Automation is crucial these days, with IT environments that are too complex and often need to scale too quickly for system administrators and developers to keep up if they had to do everything manually.
In simple words, it frees up time and increases efficiency. And also it is rapidly rising to the top in the world of automation tools.
Ansible provides the following capabilities as per:
Provisioning: setting up the environment and also resources.
Configuration management: managing all configuration files.
Application deployment: deploying of application with human readable playbooks.
Continuous delivery: creating a CI/CD pipeline.
Security automation: using modules, roles and playbooks to automate security.
Orchestration: combining all different configurations and automation tasks under one umbrella.
Ansible is one of the most popular automation tool among Software engineers, Ansible is the first choice for the Automation process, and also Ansible is called as “Darling” of DevOps. Ansible does a great job of automating Docker and operationalizing the process of building and deploying containers.
If you’re someone from a traditional IT system, for example, it can be hard to add container-tooling functionality. But Ansible removes the need to do processes manually.
Future in Ansible

As we discuss earlier using Ansible with Docker simplify your processes by allowing you to work with containers and to automate all that work, It’s no wonder the Ansible-Docker combination is so popular. And learning how to use Ansible with Docker won’t just benefit your organization, it also benefits you on your Payscale, according to Payscale, the average salary of a developer with Ansible skills is $130,000 per year, and some developers earn even more.
According to Dice, Ansible is the highest-paying DevOps skill. Ansible is probably the only widely-used automation tool that allows us to describe the whole deployment uniformly, Ansible Collections play a central role in Ansible’s flexibility. They provide, among other things, integrations with cloud providers that unlock cloud-management capabilities.
So Ansible is not going anywhere and have lots of job profile and stable career with Ansible.
If you want learn more about Ansible and want a Certification Course of Ansible I would like to suggest you DevOpsSchool.com, one of the top institute for Ansible Certification Training Course to kick start your career in the field of Automation.
I hope you find this particular blog helpful and informative about Ansible.
Thank You!!