In this blog, I am creating floating text animation & text rotator animation using HTML & CSS. So, Let’s create an index.html & style.css below-


In this blog, I am creating floating text animation & text rotator animation using HTML & CSS. So, Let’s create an index.html & style.css below-


The practice of cloud computing gradually increase over the years as the COVID-19 pandemic caused massive disruption to businesses around the world. If you are a beginner to the world of cloud computing, and wonder to select a cloud platform to get started with learning cloud. At present there are so many Cloud platform and it is quite difficult to differentiate and choose the write one.
Both AWS and Azure are solid performer in almost 99% of the use cases and one of the big name between cloud providers. In this blog will discuss about AWS and every aspect about its certification and is it worth it to learn AWS in 2021-22? Lets first discuss about AWS-
What is AWS?

AWS well known as Amazon Web Services is a secure cloud services platform, which allow users to compute power, database storage, content delivery and other work activities to help businesses scale and grow. AWS offer more services and features in compare to others cloud provider in every aspect from infrastructure technologies to emerging technologies.
It has the largest community with more than millions of active customers and thousands of partners all around the globe.
Advantages of AWS:
Before we go into the question that is it worth it to learn AWS in 2021-22? It is important to be clear on what certification AWS offered.
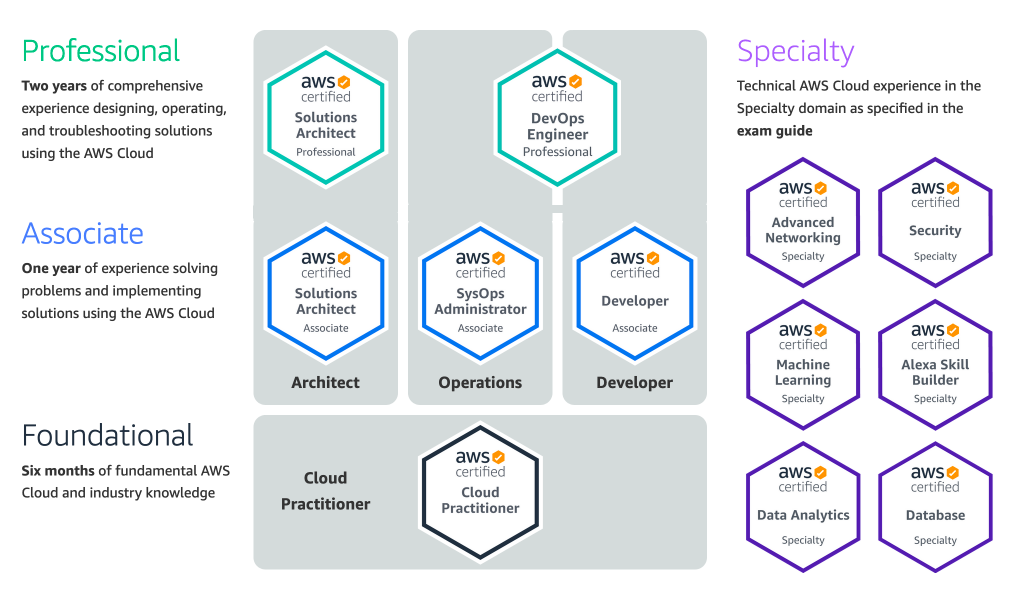
The certifications are mainly divided into 4 paths based, Foundational, Architect, Operation and Developer. All these certification are described in more detail below.
Foundational Level
Architect Level
Operation Level
Developer Level
Specialty Certifications
There are also five specialty AWS certifications:
These above Certification by AWS is completely hands-on and designed in a way to help you become technical expertise in your selective path of certification.
Reasons Why AWS Certifications Are Worth It in 2021
There is no surprise that cloud computing experts with AWS certifications are gradually in high demand with time. So, if the questions is still in your mind that “Is it worth it to learn AWS in 2021-22?” the answer is a big YES!
Here are some more reasons why AWS certifications are worth in 2021-22:
Where to Start
Best institute alongside with many free Training resources are a great way to get the ball rolling in your cloud certification journey, they offering comprehensive AWS certification course by top experts of the programme. They trained and prepare you for the AWS certification exam. You will also learn the best practices to be followed while working on AWS projects in the industry.
This Certification is completely hands-on and designed in a way to help you become technical expertise. If you want this kind of effective training and so many free Training resources to start your Journey and boost your career in the field of cloud computing then I would like to suggest you some institute that can meet your expectations.
By DevOpsScool.com
By ScmGalaxy.com
I hope this particular information about AWS is helpful and informative.
Thank you !!
Given that the LAMP stack is based on Linux and that the entire open-source community is working to enhance it, it is also deemed secure. All security updates and patches are accessible as an automatic unattended install on an Ubuntu VPS as soon as they are released in the Ubuntu repos, so make sure you configure your system to automatically install them if you are concerned about security.If you don’t enable this option on your server and don’t manually install the latest upgrades and patches, you’re placing your server at risk of being hacked.
Install the unattended-upgrades package to enable automatic unattended upgrades.
sudo apt-get install unattended-upgrades
Edit the /etc/apt/apt.conf.d/50unattended-upgrades file to specify which package categories should be upgraded automatically.
Another very important aspect of overall security is having a properly set firewall. ufw is Ubuntu’s default firewall configuration tool, and it’s turned off by default. You can use the following commands to enable ufw:
sudo ufw enable
Allow essential services like OpenSSH and Apache to be accessed:
sudo ufw allow 22
sudo ufw allow 80
sudo ufw allow 443
It’s simple to grant access to other services. Simply change the port number in the samples above to the port number of the service you wish to enable access to, and you’re done. Even if the machine is rebooted, the firewall rules will remain active.
If you have active services which you are not using, you can simply disable them. For example, if you have service like Dovecot up and running on your server and you are not using it at all, stop and disable the service using the following commands:
sudo systemctl stop dovecot.service
sudo systemctl disable dovecot.service
Fail2ban is a service that scans log files for excessive login failures and blocks the IP address that is displaying malicious behaviour. If you don’t use two-factor or public/private authentication techniques on services like OpenSSH, this service comes in handy. Run the following command to install Fail2ban:
sudo apt-get install fail2ban
Make a copy of the default configuration file so you can make modifications without worrying about system updates overwriting them:
sudo cp /etc/fail2ban/jail.conf /etc/fail2ban/jail.local
Edit the jail.local file:
sudo nano /etc/fail2ban/jail.local
The [sshd] block should look something like this:
[sshd]
enabled = true
port = ssh
filter = sshd
logpath = /var/log/auth.log
maxretry = 5
bantime = 600
To make the modifications take effect, save the file and restart Fail2ban:
sudo systemctl restart fail2ban.service
Enable Fail2ban on system boot:
sudo systemctl enable fail2ban.service
The default Apache setup exposes a great deal of sensitive data that can be used against the service. It’s critical to keep this information secret, therefore make a configuration file for your new settings:
sudo nano /etc/apache2/conf-available/custom.conf
Copy and paste the following text:
ServerTokens Prod
ServerSignature Off
TraceEnable Off
Options all -Indexes
Header unset ETag
Header always unset X-Powered-By
FileETag None
If it isn’t already enabled, enable the Apache headers module:
sudo a2enmod headers
Enable the following settings:
sudo a2enconf custom.conf
To make the modifications take effect, restart Apache:
sudo systemctl restart apache2.service
Mod security is a web application firewall (WAF) that may be added to Apache as a separate module. It can be used to protect a web server from a variety of threats, including SQL injections, session hijacking, cross-site scripting, and malicious user agents. Run the instructions following to install and enable mod security:
sudo apt-get install libapache2-modsecurity2
sudo a2enmod security2
You should setup the module and enable the OWASP ModSecurity Core Rule Set after it has been installed (CRS).
sudo mv /etc/modsecurity/modsecurity.conf-recommended /etc/modsecurity/modsecurity.conf
Then, open the /etc/modsecurity/modsecurity.conf file and edit/add the following settings:
SecRuleEngine On
SecResponseBodyAccess Off
SecRequestBodyLimit 8388608
SecRequestBodyNoFilesLimit 131072
SecRequestBodyInMemoryLimit 262144
Save and close the file. Remove the current CRS and download the OWASP CRS by using the following commands:
sudo rm -rf /usr/share/modsecurity-crs
sudo git clone https://github.com/SpiderLabs/owasp-modsecurity-crs.git /usr/share/modsecurity-crs
cd /usr/share/modsecurity-crs
sudo mv crs-setup.conf.example crs-setup.conf
Edit the security2.conf file in /etc/apache2/mods-enabled/security2.conf. It should resemble the following:
<IfModule security2_module>
SecDataDir /var/cache/modsecurity
IncludeOptional /etc/modsecurity/*.conf
IncludeOptional "/usr/share/modsecurity-crs/*.conf"
IncludeOptional "/usr/share/modsecurity-crs/rules/*.conf
</IfModule>
Finally, to make the modifications take effect, restart Apache:
sudo systemctl restart apache2.service
Mod evasive is an Apache module that can prevent DoS (Denial of Service), DDoS (Distributed Denial of Service), and brute-force assaults on the web server. Run the following command to install mod evasive on your server:
sudo apt-get install libapache2-mod-evasive
Open the default configuration file /etc/apache2/mods-enabled/evasive.conf and edit the settings to look like those below:
<IfModule mod_evasive20.c>
DOSPageCount 5
DOSSiteCount 50
DOSPageInterval 1
DOSSiteInterval 1
DOSBlockingPeriod 600
DOSLogDir "/var/log/mod_evasive"
</IfModule>
The file should be saved and closed. Make a folder for the log files:
sudo mkdir /var/log/mod_evasive
sudo chown -R www-data: /var/log/mod_evasive
Restart Apache:
sudo systemctl restart apache2.service