In this blog, I am creating a creative rotated text border effect & social media icons hover transforms using HTML & CSS. So, Let’s create an index.html & style.css below-





In this blog, I am creating a creative rotated text border effect & social media icons hover transforms using HTML & CSS. So, Let’s create an index.html & style.css below-





In this blog, I am creating a creative double face card hover effect & creative expandable card effect using HTML & CSS. So, Let’s create an index.html & style.css below-





In this blog, I am creating creative a border card hover effect with a background translation using HTML & CSS. So, Let’s create an index.html & style.css below-

Azure DevOps has a great growth in coming times and promising future. The practise of DevOps is increasing day by day in IT domain. The demand for the Azure DevOps is well shown in the salary structure in India for them. This particular blog is all about the future of Azure DevOps in different areas of the IT industry and opportunities you have.
Azure DevOps is a modern DevOps tool which is used to developing, testing and deploying modern apps through optimized cycle to provide a quality delivery of applications to users. It provides so many of tool which can helpful in tracking software building progress and also helpful for taking decision to deliver great software to the end users. The main thing is Azure DevOps services are not dependent on cloud platform.
Benefits of Azure DevOps
Azure DevOps allows their users to develop, deploy, and monitor code without opening multiple interfaces and you can also manage all of this from one view and bring ease to the customers.
Some of the main benefits are:
Career opportunity as an Azure DevOps Engineer?

Azure DevOps Engineers are responsible for defining and implementing a robust, scalable, pragmatic and realistic cloud solution that works for our clients. Design and implement cloud solutions which are secure, scalable, resilient, monitored, auditable and cost optimized. So what are the options in front of you when you complete your Certification as an Azure DevOps Engineer?
Here are a few job roles that you can fill:
Salary of an Azure DevOps Engineer
So many big fortune companies along with many start-ups or small businesses are required with an Azure DevOps Engineer who is certified. Not to worry about the job you get or salary offer to you after the completion as a certified Azure DevOps Engineer, just focus on enhancing your real-time experience if you planned to be a part of any big renowned organizations and dream job with the salary you wished for.
Let us have a look at a range of salaries across the globe.
As an Azure DevOps engineer, the national average salary is $105,114.
Conclusion
The future of Azure DevOps is very promising, and many more companies are set to accept this methodology. Just not to worry about the job you get or salary offer to you after the completion as a certified Azure DevOps Engineer, just focus on enhancing your real-time experience, practical knowledge if you planned to be a part of any big renowned organizations.
I hope you find this particular Blog helpful, we have discussed ideas around DevOps future scope and how it is going to revolutionize the industry further.
If you are interested to become an Azure DevOps, I would like to suggest you DevOpsSchool.com, one of the best institute for Azure DevOps training and certification, both in online and offline classroom mode.
Introduction
Node.js could be a platform designed on Chrome’s JavaScript runtime for simply building quick and scalable network applications. Node.js uses an event-driven, non-blocking I/O model that creates it light-weight and efficient, excellent for data-intensive time period applications that run across distributed devices.
Node.js is an open-source, cross-platform runtime setting for developing server-side and networking applications. Node.js applications are written in JavaScript and maybe run among the Node.js runtime on OS X, Microsoft Windows, and Linux.

Node. js could be a platform designed on Chrome’s JavaScript runtime for simply building quick and scalable network applications. Node. js uses an event-driven, non-blocking I/O model that creates it light-weight and efficient, excellent for data-intensive time period applications that run across distributed devices.
How does Node.js work?
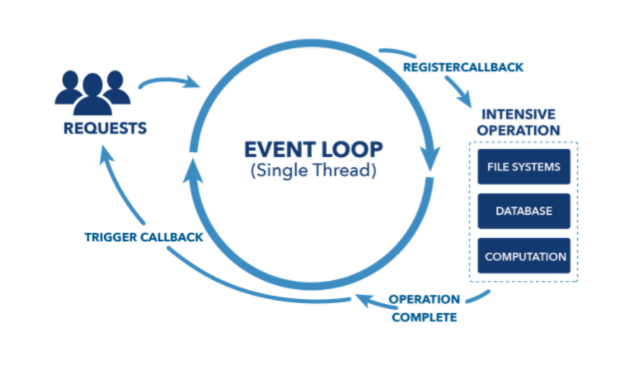
First of all just like other languages node comes with packages and modules. These are libraries of functions that we can import from npm (node package manager) into our code and utilize. Node. js is that the JavaScript runtime surroundings that’s supported Google’s V8 Engine for example with the assistance of Node. js we are able to run the JavaScript outside of the browser js is that it’s single-threaded, supported event-driven design, and non-blocking supported the I/O model.
Why is node js so popular?
Node. js will handle several concurrent requests. this is often the most reason it quickly became popular among developers and huge corporations. It will handle several simultaneous requests while not straining the server.
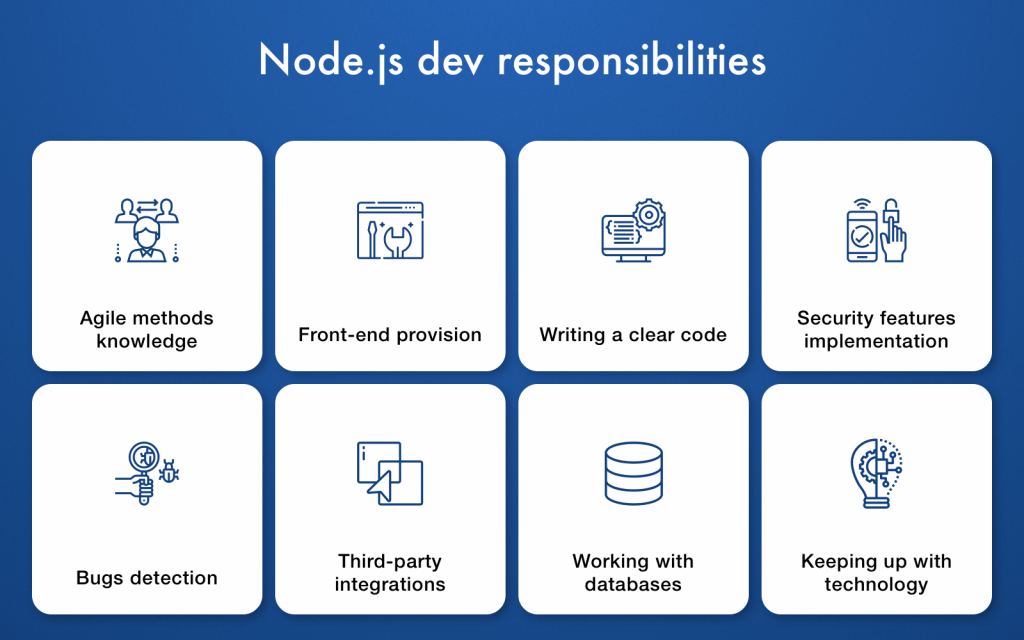
Role of a Node.js developer:

A Node. js developer is answerable for writing server-side internet application logic in JavaScript and/or variants of it, like CoffeeScript, IcedCoffeeScript, etc, js developer is answerable for writing server-side internet application logic in JavaScript and/or variants of it, like CoffeeScript, IcedCoffeeScript, etc.
Node.js Developer duties:
Responsibilities of Node.js Developers:
Single-Threaded but Highly Scalable − Node.js uses a single-threaded model with event looping. The event mechanism helps the server to reply in a non-blocking way and makes the server extremely scalable as against ancient servers that produce restricted threads to handle requests. Node.js uses a single-threaded program and therefore the same program will offer service to a far larger range of requests than ancient servers like Apache HTTP Server.
No Buffering − Node.js applications never buffer any data. These applications simply output the data in chunks.
License − Node.js is released under the MIT license.
The Benefits of Node.js:
What is the scope of node JS?

Node.js could be a runtime environment that permits you to write down server-side applications in JavaScript. PHP could be a server-side language. attributable to that, you’ll get to try PHP with a frontend language, sometimes a mix of HTML, CSS, and JavaScript, to make full-stack internet apps.
Node.js Developer Course:
Js Developer Course covers the basics of Node before diving deep into nice tools like specific, Mongoose, and MongoDB. the whole course is predicated around one goal: Turning you into an expert Node developer capable of developing, testing, and deploying real-world production applications.
Node.js Developer requirements and qualifications:
Conclusion
Node.js is, while not a doubt, one of all the additional interesting technologies in use nowadays, and it’s full-grown into one of all the foremost popular platforms used for internet applications, services, and desktop apps. It’s my hope that when looking at this course, you currently have a solid foundation to begin writing your own Node applications.
If you wanna learn, and from all of us here at DevOpsSchool, thank you for watching!