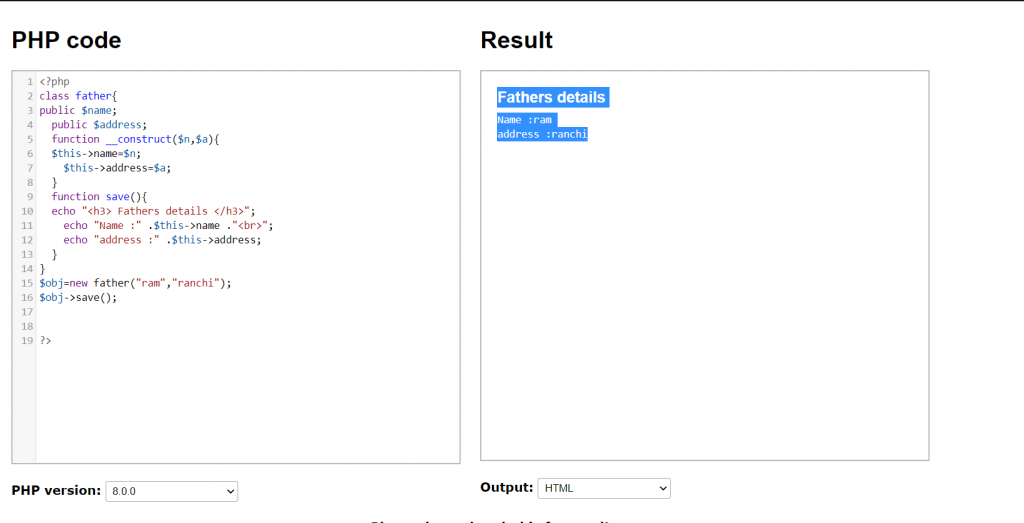
What is Traits?
- Code is shortened by using Traits.
- One code is used everywhere just by writing the trait function.
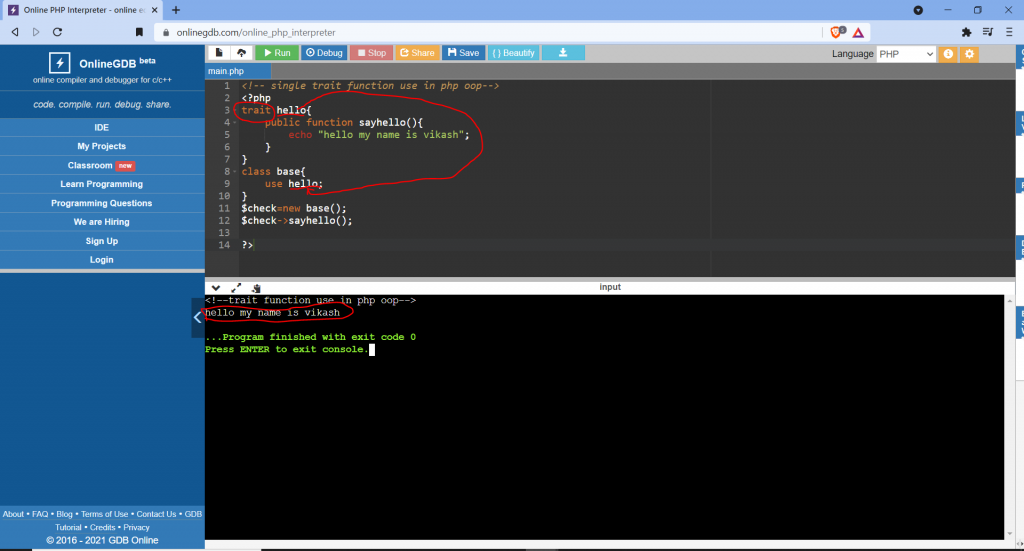
Example :
Output:
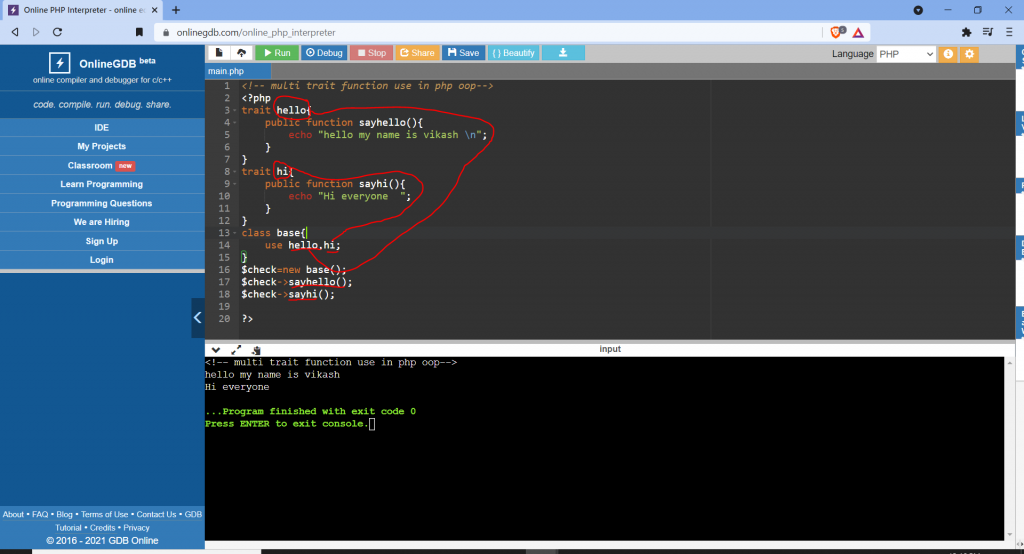
Multi traits use example:
Output:


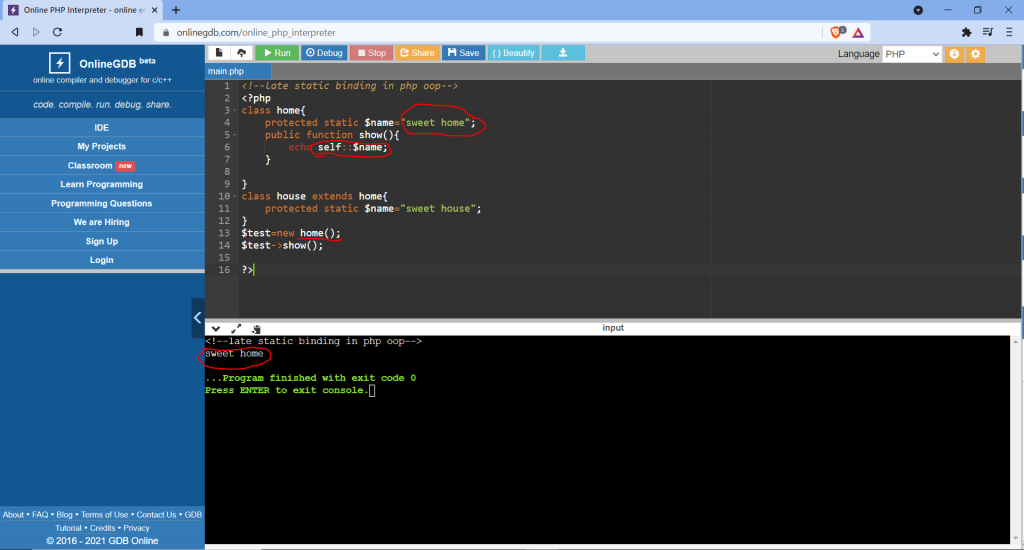
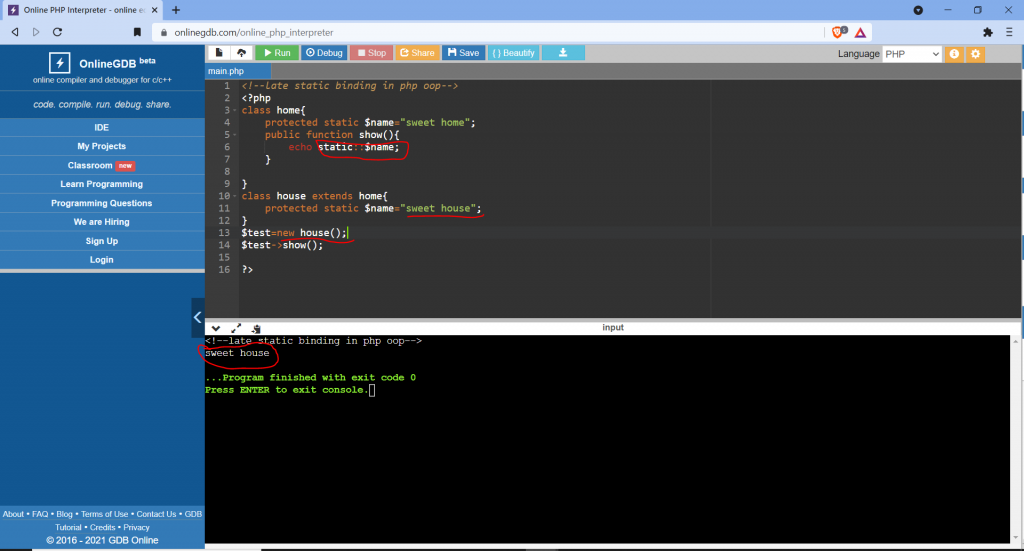
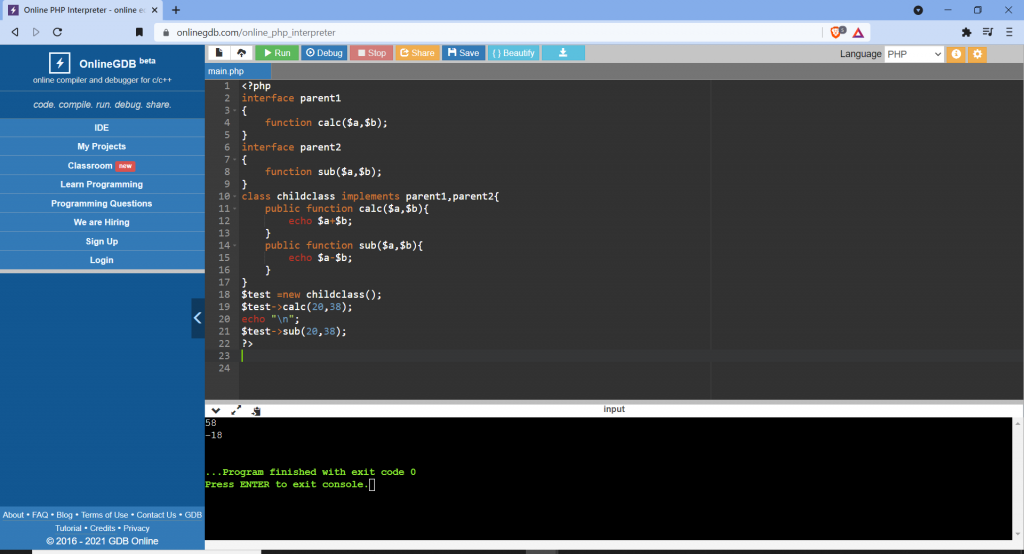
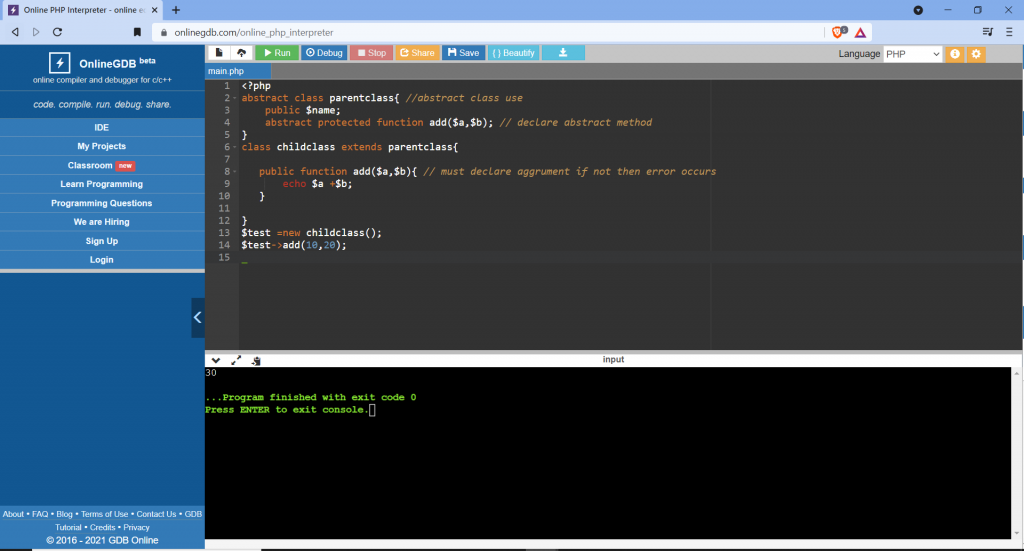
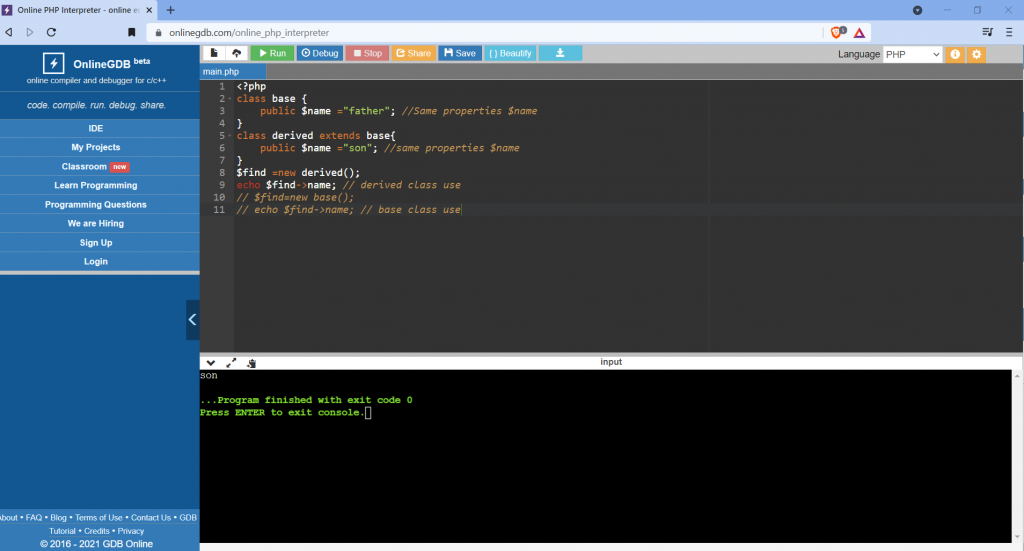
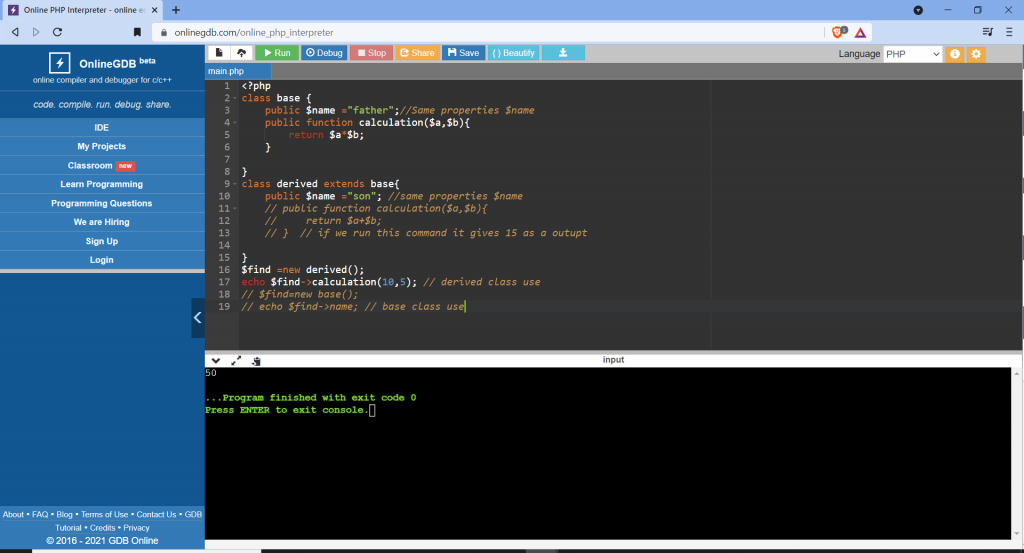
Restrictions on properties and methods.
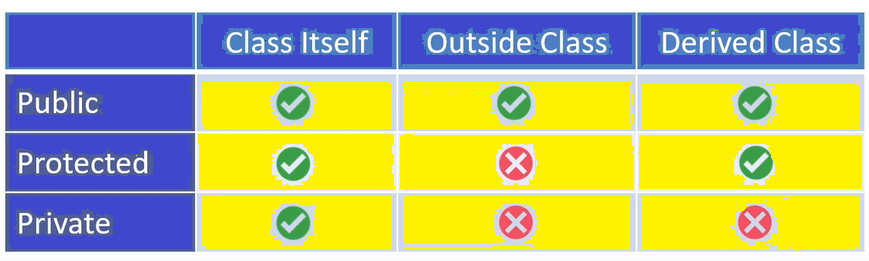
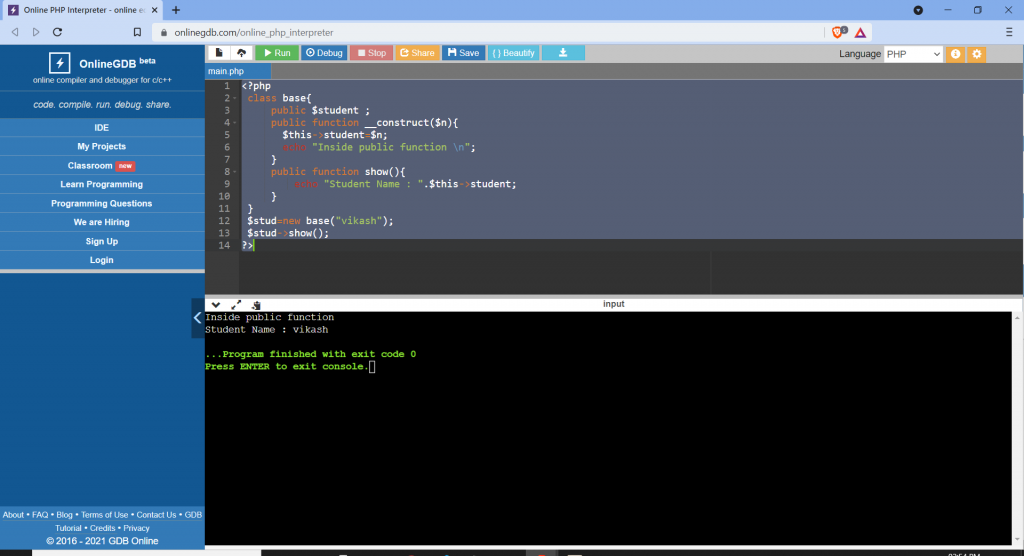
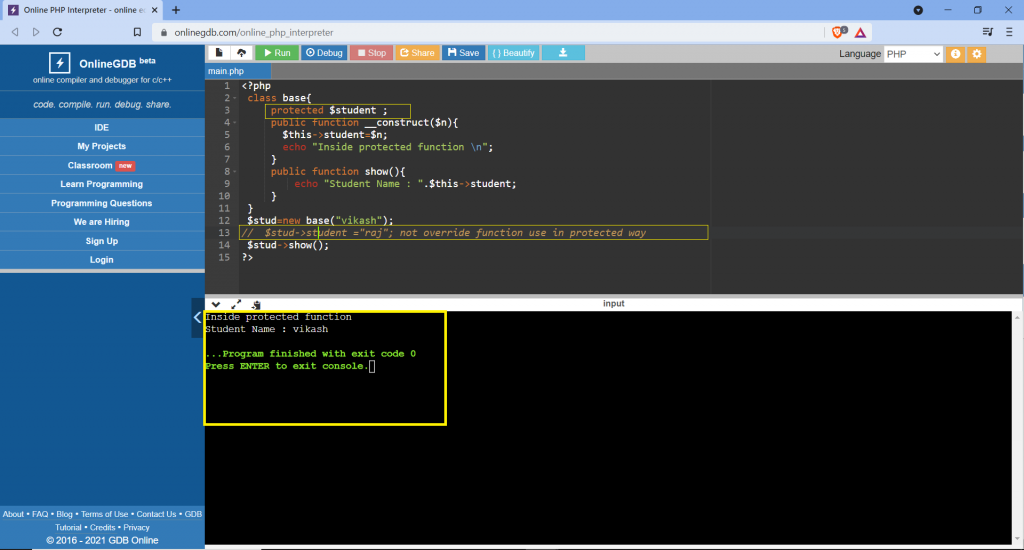
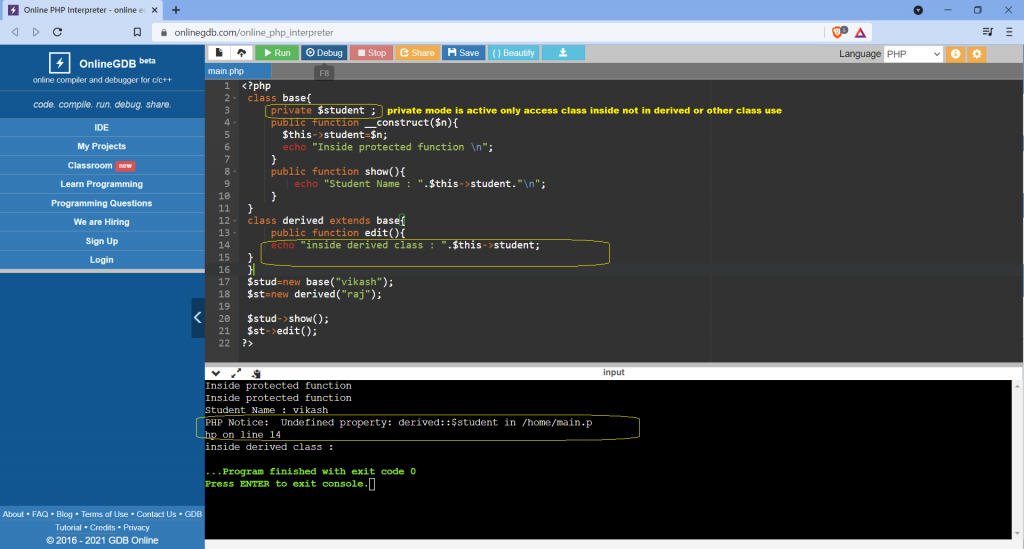
class school {
}
class students extends school {
}
$sch =new school (); // only use class school
$stu = new students (); // use both class school students (properties and methods)
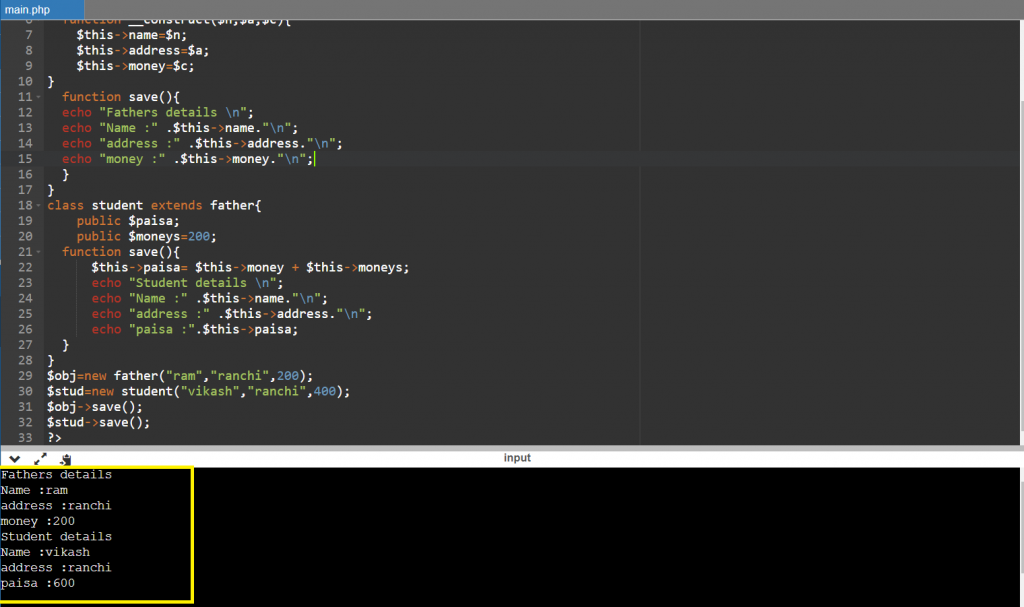
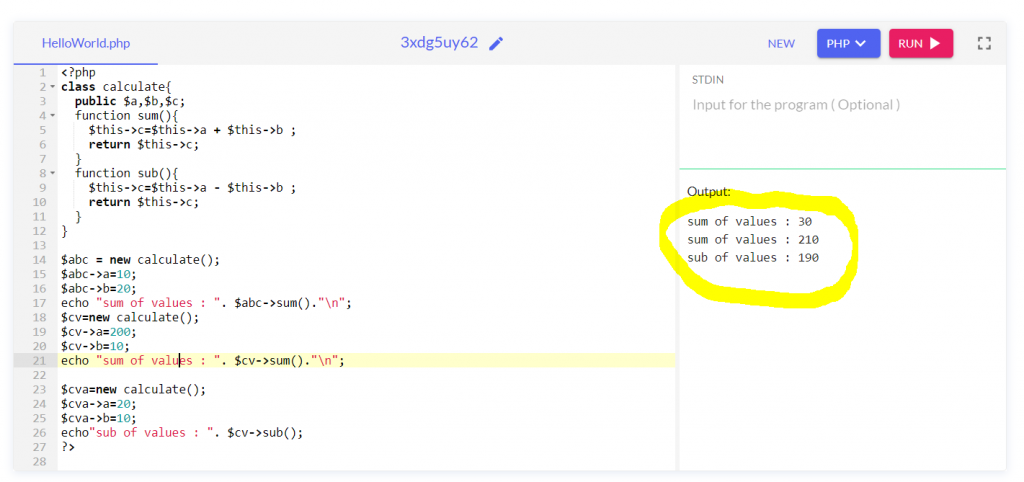
properties like :-
$a;
$b;
$c;
$d;
Methods like :-
sum(){
$c=$a+$b;
return $c;
}
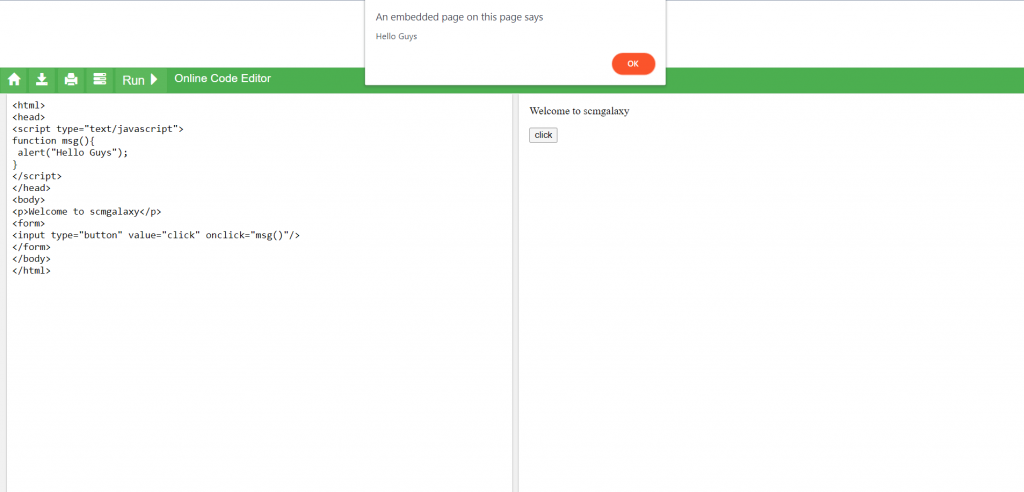
Example of javaScript using inside html between body tag.
Example to use javaScript between head tag in html.
We can create external JavaScript file and embed it in many html page. If you want to run the same JavaScript on several pages in a web site, you should create an external JavaScript file, instead of writing the same script over and over again.
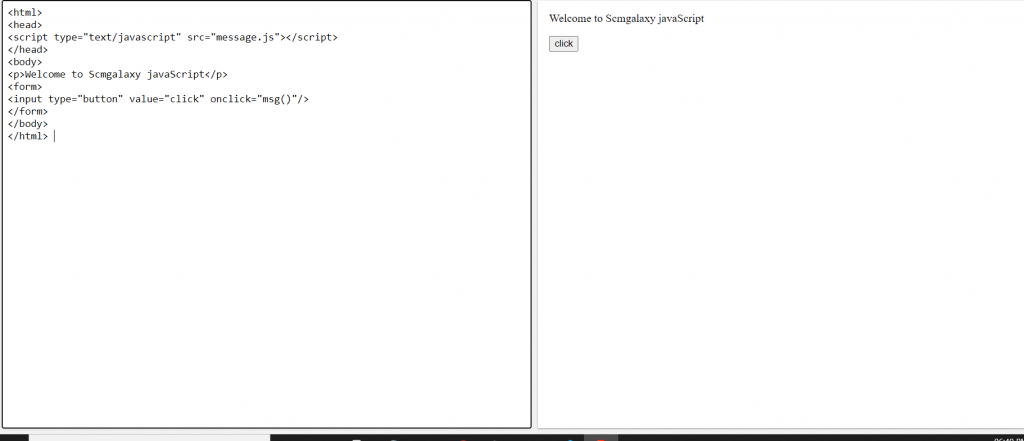
There are following features of js :-
JavaScript is used to create interactive websites. It is mainly used for:
Hello JavaScript by JavaScript